In today’s digital age, websites are critical assets for businesses and individuals alike. They serve as platforms for communication, commerce, and information dissemination. However, the increasing reliance on websites has also made them prime targets for cyber-attacks. To protect websites from these threats, various security measures are employed, one of which is the Website Application Firewall (WAF). This blog post aims to provide a comprehensive yet straightforward explanation of what a WAF is, how it works, and why it is essential for website security.
Table of Contents
Understanding the Basics
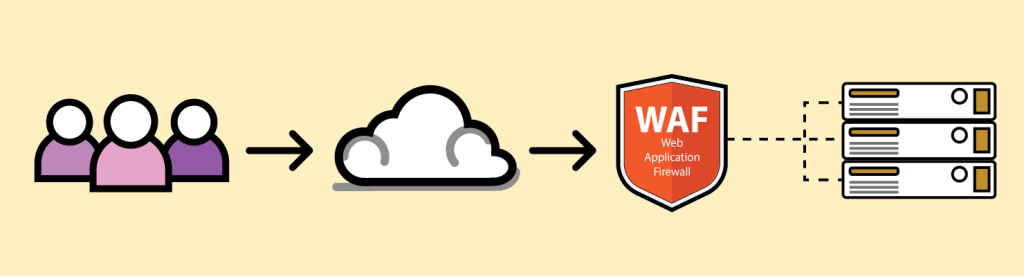
A Website Application Firewall (WAF) is a security solution designed to protect web applications by filtering and monitoring HTTP traffic between a web application and the Internet. Unlike traditional firewalls that defend against network-level attacks, a WAF focuses on the application layer (Layer 7 of the OSI model), which is where most vulnerabilities and attacks occur.

How Does a Website Application Firewall (WAF) Work
A WAF acts as a shield between a web application and the internet. It analyzes incoming and outgoing web traffic, looking for malicious activity and blocking harmful requests before they can reach the application. Here’s a breakdown of how a WAF functions:
- Traffic Monitoring and Filtering: A WAF inspects every HTTP request and response that passes through it. It uses predefined rules and algorithms to identify and filter out malicious traffic, such as SQL injection, cross-site scripting (XSS), and other common web attacks.
- Behavioral Analysis: Some advanced WAFs employ machine learning and behavioral analysis to detect anomalies in traffic patterns. By understanding what normal traffic looks like, these WAFs can identify and block unusual or suspicious activities.
- Signature-Based Detection: WAFs maintain a database of known attack signatures (patterns of malicious code or behavior). When incoming traffic matches one of these signatures, the WAF blocks the request.
- Whitelisting and Blacklisting: Administrators can configure WAFs to allow (whitelist) or block (blacklist) specific IP addresses, countries, or types of requests. This customization enhances the security of the web application.
Types of Website Application Firewalls (WAFs)
There are three main types of WAFs, each with its own deployment method:

- Network-Based WAF: This type of WAF is typically hardware-based and is installed directly in the network infrastructure. It provides high performance and low latency but can be costly and complex to deploy.
- Host-Based WAF: Installed directly on the web server, host-based WAFs are software solutions that integrate closely with the application. They offer granular control and customization but can consume significant server resources.
- Cloud-Based WAF: Cloud-based WAFs are hosted by a third-party service provider. They are easy to deploy and manage, offering scalability and flexibility. However, they may introduce some latency due to the additional network hops.
Key Features of a WAF
When evaluating a Website Application Firewall (WAF), consider the following key features that contribute to its effectiveness:
- Attack Detection and Prevention: A robust WAF should be capable of detecting and preventing a wide range of web attacks, including SQL injection, XSS, CSRF (Cross-Site Request Forgery), and DDoS (Distributed Denial of Service) attacks.
- Customizable Rules: The ability to create and modify security rules allows administrators to tailor the WAF to the specific needs of their web application.
- Logging and Reporting: Comprehensive logging and reporting capabilities enable administrators to monitor WAF activity, analyze incidents, and ensure compliance with security policies.
- SSL/TLS Support: Since many web applications use HTTPS for secure communication, a WAF must be able to inspect and filter encrypted traffic without compromising security.
- Scalability: A WAF should be able to scale to accommodate the growing traffic and complexity of web applications.
- Performance: The WAF should operate with minimal impact on the performance and latency of the web application.
Why is a Website Application Firewall (WAF) Essential?
The importance of a Website Application Firewall (WAF) in today’s cybersecurity landscape cannot be overstated. Here are several reasons why deploying a WAF is crucial for protecting web applications:
- Protection Against Common Attacks: Web applications are frequently targeted by various attacks. A WAF provides a strong defense against these threats, safeguarding sensitive data and maintaining the integrity of the application.
- Compliance Requirements: Many industries have regulatory requirements that mandate the protection of web applications. Implementing a WAF helps organizations meet these compliance standards, such as PCI DSS for payment card data security.
- Business Continuity: Cyber-attacks can lead to downtime, data breaches, and loss of customer trust. A WAF helps ensure business continuity by mitigating the risk of successful attacks.
- Cost-Effective Security: While a WAF is an investment, it is generally more cost-effective than dealing with the aftermath of a successful cyber-attack, which can include data recovery, legal fees, and reputational damage.
- Peace of Mind: Knowing that your web application is protected by a WAF allows you to focus on your core business activities without constantly worrying about security threats.
Best Practices for Implementing a WAF
To maximize the effectiveness of a Website Application Firewall (WAF), follow these best practices:
- Regular Updates: Keep your WAF up-to-date with the latest security patches and attack signatures to ensure it can defend against emerging threats.
- Monitor Traffic Continuously: Regularly monitor web traffic and WAF logs to detect and respond to potential security incidents promptly.
- Fine-Tune Rules: Continuously review and adjust the WAF’s security rules to align with the evolving threat landscape and the specific needs of your web application.
- Test for Vulnerabilities: Conduct regular security assessments and penetration testing to identify and address vulnerabilities that a WAF might not catch.
- Educate and Train Staff: Ensure that your IT and security teams are well-versed in WAF management and web application security best practices.
Conclusion
A Website Application Firewall is a critical component of web application security. By filtering and monitoring traffic, detecting and blocking attacks, and providing customizable protection, a WAF helps safeguard web applications from a myriad of threats. Whether you choose a network-based, host-based, or cloud-based WAF, implementing this security measure is a proactive step towards ensuring the safety and reliability of your web application. With cyber threats continually evolving, having a WAF in place not only enhances security but also provides peace of mind and supports business continuity.



